BankBot Android malware sneaks into Google Play Store for the third time
The Google Play Store is unintentionally distributing a particular form of Android banking malware for the third time this year.
BankBot first appeared in the official Android marketplace in April this year, was removed, and then was discovered to be have returned in September before being removed again. Now BankBot has appeared in the Google Play store yet again, having somehow bypassed the application vetting and security protocols for a third time.
BankBot is designed to steal banking credentials and payment information. It tricks users into handing over their bank details by presenting an overlay window which looks identical to a bank's app login page.
The malware is capable of identifying a variety of financial and retail mobile apps on the infected devices and tailors the phishing attack to display a fake version of the banking app the victim uses, if the target bank is recognized by the malware.
If the user uses text messages as a form of two-factor authentication, the malware is also capable of monitoring these in order to provide attackers with all the information they need to raid the victim's banking information
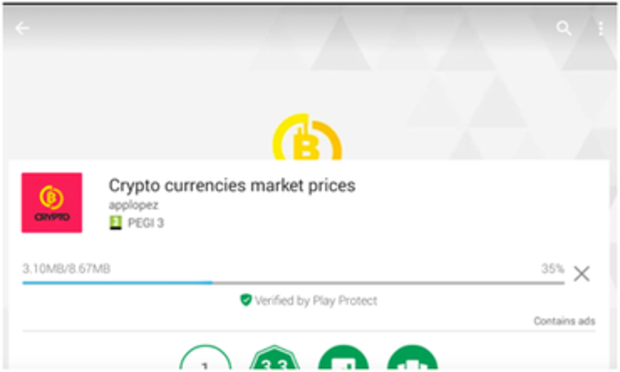
Discovered by researchers at RiskIQ, the latest version of BankBot to infiltrate the Google Play Store is disguised as an app called "Crypto currencies market prices" -- complete with a phony "Verified by Play Protect" logo in order to make it look as if it is a known and trusted app.
To the user, the app looks as if it is designed for comparing cryptocurrency prices with other forms of money, and is even equipped with a legitimate application for cryptocurrency monitoring -- which is partly how the app manages to bypass Play Store security checks.
By giving the user an app which actually works, the group behind it are increasing the likelihood of achieving their goals, as a user is likely to uninstall an app which crashes or doesn't work.
When initially installed on the device, the app asks for a variety of intrusive permissions, including the ability to read and send messages, access the internet, and write to external storage.
These ultimately provide BankBot with all the permissions it needs to overlay fake login screens, then extract the stolen information and send it back to the attacker -- be to make purchases for themselves, or to sell on the stolen credentials.
The attackers behind BankBot update it regularly. Since first appearing earlier this year, the malware has gained improved code obfuscation, a more sophisticated payload dropping functionality, and the ability to exploit Android's Accessibility Service in a similar way to other forms of mobile banking malware.
Since being detected, the malware distributing "Crypto currencies market prices" app has been removed from the Google Play Store. The malicious app was downloaded a few thousand times.
Google maintains that it keeps the vast majority of its 1.4 billion Android users safe from malware.
But this marks yet another embarrassing incident for Google when it comes to Play Store security. Recently a fake version of WhatsApp was recently downloaded by over a million users before it was discovered and removed.
ZDNet has attempted to contact Google for comment on the latest BankBot discovery, but had not received a response at the time of publication.
This story originally appeared on ZDNet.